PE-sieve is my open source tool based on libpeconv . The tool is dedicated to Windows, all versions are supported, starting from XP.
It scans a given process, searching for potentially malicious implants and patches within the process space. When found, it dumps the modified/suspicious PE along with a report in JSON format, detailing about the found indicators.
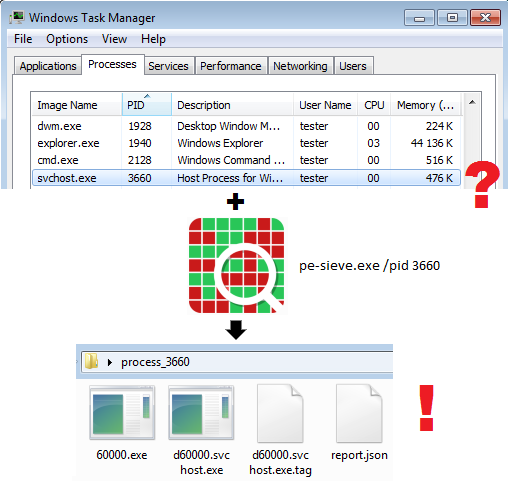
Currently it detects inline hooks, hollowed processes, Process Doppelgänging, injected PE files, and more. In case if the PE file was patched in the memory, it gives a detailed report about where are the changed bytes (and few other properties).
PE-sieve is available in 2 flavors – as standalone executable, and as a DLL. The DLL version is a base of my other project: HollowsHunter – that makes an automated scan of all the running processes. More about it in the further part of the post.
Complete documentation is available on project Wiki.
The tool is under rapid development, so expect frequent updates.

Tested and certified by softpedia.com.

Hi, thanks for your paper! I actually have a problem here. Your tool seems can dump the payload of the process hollowing? But I tried that with a process hollowing malware here https://www.hybrid-analysis.com/sample/e30b76f9454a5fd3d11b5792ff93e56c52bf5dfba6ab375c3b96e17af562f5fc?environmentId=100. It seems I can’t dump the payload. I just stop before the “resumethread”. And I tried to use your tool to dump both the child process and the original one and failed. Can you give me some ideas?
Hi, I checked your sample and had no problems unpacking it. This is what I did: https://www.youtube.com/watch?v=7xtxOD1LX7U
Hi,
Can the tool be used on a memory dump file, as not all systems’ owners allow live forensics to be done on their live systems?
Thanks!
Hi, actually, this feature is on my TODO list and will be implemented in the future (https://twitter.com/hasherezade/status/946034099294277632). You can also create a github issue for me, with a feature request and more detailed description (https://github.com/hasherezade/pe-sieve/issues)
Thank you very much!
Pingback: PE-sieve, a command line tool for investigating inline hooks – So Long, and Thanks for All the Fish
Pingback: Loki v0.28.2 – Simple IOC and Incident Response Scanner | SecTechno
Nice I wonder if this can detect meltdown?
no, it is for something else: it just detects code implants. more details about it you can find in my presentation: https://speakerdeck.com/hshrzd/pe-sieve-detecting-hooking-and-code-implants
Pingback: Extracting Malware from Memory with Hollows_Hunter – SecurityLiterate.com
Pingback: The Use – and Abuse – of DotNet Files, and the Value of FortiResponder Automation in the Threat Analysis Process – Computer Security Articles
Pingback: ▷ Loki: Simple IOC and Incident Response Scanner » GeekScripts
Nice work !!keep up . I would like to follow you , why not do some projects with you.